Post updated in December 2025
ConfigureDefender utility for Windows 10/11.
New stable version 4.1.0.0 is available on the developer website (updated in February 2025):
https://github.com/AndyFul/ConfigureDefender
Softpedia:
https://www.softpedia.com/get/PORTABLE-SOFTWARE/System/System-Enhancements/ConfigureDefender.shtml
WinGet (ver. 4.0.1.1)

 winstall.app
winstall.app
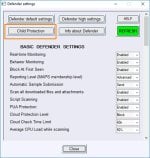
The ConfigureDefender utility is a GUI application for viewing and configuring important Defender settings on Windows 10/11. It mostly uses PowerShell cmdlets (with a few exceptions). Furthermore, the user can apply one of three predefined settings: Default, High, or Max. Applying settings requires restarting the computer.
High settings are recommended for most users.
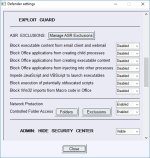
The Max protection is mostly set to block anything suspicious via Attack Surface Reduction, Controlled Folder Access, SmartScreen (set to Block), and the 0-tolerance cloud level.
ConfigureDefender utility is part of the Hard_Configurator project, but it can be used as a standalone application.
Some reviews:
Windows 10 Defender's hidden features revealed by this free tool (bleepingcomputer.com)
Windows Defender configuration tool ConfigureDefender 3.0.0.0 released - gHacks Tech News
ConfigureDefender utility for Windows 10/11.
New stable version 4.1.0.0 is available on the developer website (updated in February 2025):
https://github.com/AndyFul/ConfigureDefender
Softpedia:
https://www.softpedia.com/get/PORTABLE-SOFTWARE/System/System-Enhancements/ConfigureDefender.shtml
WinGet (ver. 4.0.1.1)

Install ConfigureDefender with winget - winstall
Utility for configuring Windows 10 built-in Defender antivirus settings.
The ConfigureDefender utility is a GUI application for viewing and configuring important Defender settings on Windows 10/11. It mostly uses PowerShell cmdlets (with a few exceptions). Furthermore, the user can apply one of three predefined settings: Default, High, or Max. Applying settings requires restarting the computer.
High settings are recommended for most users.
The Max protection is mostly set to block anything suspicious via Attack Surface Reduction, Controlled Folder Access, SmartScreen (set to Block), and the 0-tolerance cloud level.
ConfigureDefender utility is part of the Hard_Configurator project, but it can be used as a standalone application.
Some reviews:
Windows 10 Defender's hidden features revealed by this free tool (bleepingcomputer.com)
Windows Defender configuration tool ConfigureDefender 3.0.0.0 released - gHacks Tech News
Attachments
Last edited: