Did you send the sample?
Malware Analysis Capcut fake stealer
- Thread starter likeastar20
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
- Status
- Not open for further replies.
Did you send the sample?
This is the sample you posted this morning
Web filtering could also have blocked all connections, when provided by a vendor with prompt threat intelligence. Like for Check Point for example, all C&Cs were known and blocked.But once again an Outbound alerting Firewall would have noticed a connection out to Command
After seeing all of these stealers that both Kaspersky and Harmony deal with effortlessly, I'm glad to be a user of both.Kaspersky : UDS:Trojan-PSW.Win64.Fobo.jk
Harmony : detected (PDM:Trojan.Win32.Generic)
DeepInstinct : not detected :/
Not a question related to this sample, quite often with samples posted here and other sources I follow I've noticed Kaspersky is normally quite quick at detecting it other thing I've noticed Bitdefender seem to be a bit slow at adding new detections compared to the past.
Kaspersky gets it with its behavioral detection, which then feeds into KSN as UDS:______. Bitdefender misses it without signatures.Not a question related to this sample, quite often with samples posted here and other sources I follow I've noticed Kaspersky is normally quite quick at detecting it other thing I've noticed Bitdefender seem to be a bit slow at adding new detections compared to the past.
Aside from behavioral detection, Kaspersky is pretty much at the top in writing defnitions against malware. They to this both re-actively (once a malicious file is in the Wild) as well as proactively with a division dedicated to discovering and monitoring DarkWeb groups that are writing new malware.Not a question related to this sample, quite often with samples posted here and other sources I follow I've noticed Kaspersky is normally quite quick at detecting it other thing I've noticed Bitdefender seem to be a bit slow at adding new detections compared to the past.
Their behavioral detection also tops all other home AV's and some business products. It only looses out when you compare it to other products like Checkpoint Harmony, or other EDRs, which probably use part of Kaspersky such as threat intelligence or their engine to increase effectiveness, and things topping Kaspersky are VERY FEW.Aside from behavioral detection, Kaspersky is pretty much at the top in writing defnitions against malware. They to this both re-actively (once a malicious file is in the Wild) as well as proactively with a division dedicated to discovering and monitoring DarkWeb groups that are writing new malware.
Last edited:
Another Avast miss on my end, detected by Kaspersky 
 tria.ge
tria.ge
strela | 6ef79b0d87df8031acaa5f7302001fca22f908619f1c887ce70539050c3235ce | Triage
Check this strela report malware sample 6ef79b0d87df8031acaa5f7302001fca22f908619f1c887ce70539050c3235ce, with a score of 10 out of 10.
Bitdefender Free:Another Avast miss on my end, detected by Kaspersky
strela | 6ef79b0d87df8031acaa5f7302001fca22f908619f1c887ce70539050c3235ce | Triage
Check this strela report malware sample 6ef79b0d87df8031acaa5f7302001fca22f908619f1c887ce70539050c3235ce, with a score of 10 out of 10.tria.ge
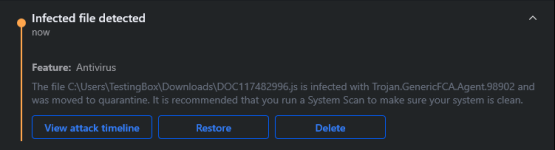
Another Avast miss on my end, detected by Kaspersky
strela | 6ef79b0d87df8031acaa5f7302001fca22f908619f1c887ce70539050c3235ce | Triage
Check this strela report malware sample 6ef79b0d87df8031acaa5f7302001fca22f908619f1c887ce70539050c3235ce, with a score of 10 out of 10.tria.ge
I quickly deployed a KTS on my VM (sorry, it's not in English, but in my native language)
Kaspersky blocked it on launch - dodgy KSN.
Kaspersky is crazy frAnother Avast miss on my end, detected by Kaspersky
strela | 6ef79b0d87df8031acaa5f7302001fca22f908619f1c887ce70539050c3235ce | Triage
Check this strela report malware sample 6ef79b0d87df8031acaa5f7302001fca22f908619f1c887ce70539050c3235ce, with a score of 10 out of 10.tria.ge
I take you block powershell, if so do you get any side effects doing that.
And blocked by behavior, even without my policy.
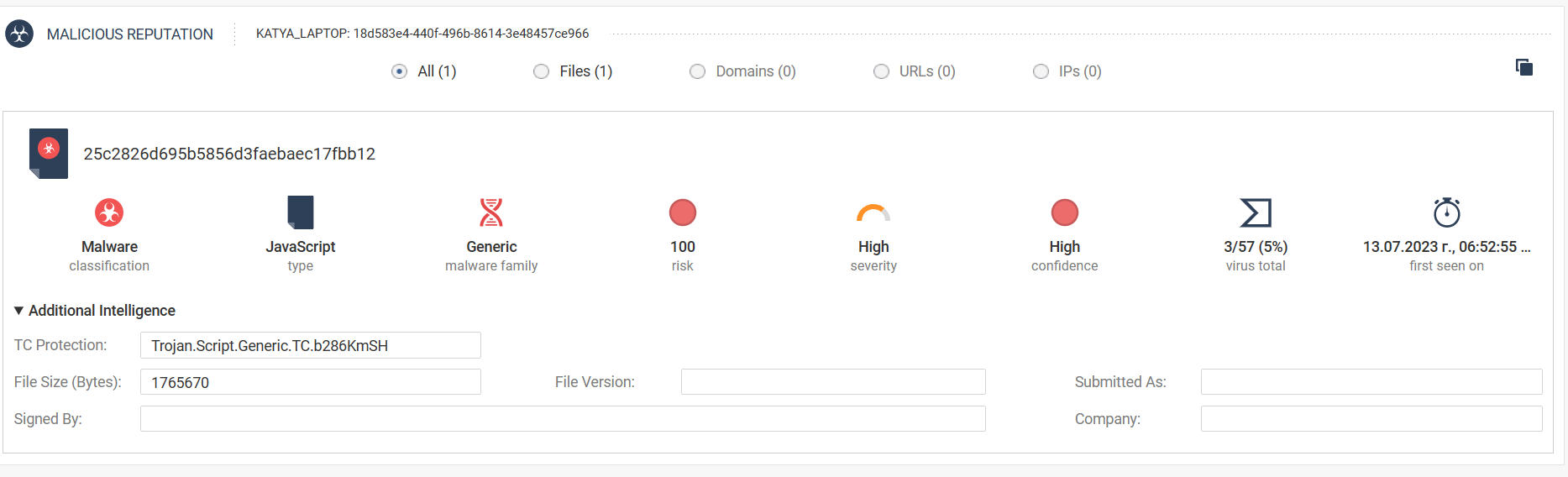
Nothing really.I take you block powershell, if so do you get any side effects doing that.
Kaspersky is crazy fr
Look above, Kaspersky detects it well.
Kaspersky is too good. Another fake game stealer using the same method(app.asar). Downloaded from itch.io, it's actually on the "New & Popular" page. On VT, Kaspersky caught it againLook above, Kaspersky detects it well.
epsilon | 962c6df0b8ca065bd5df52e06c744c7795867aaacf856798e78cf27fecf3ea9d | Triage
Check this epsilon report malware sample 962c6df0b8ca065bd5df52e06c744c7795867aaacf856798e78cf27fecf3ea9d, with a score of 10 out of 10.
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
Another one, Avast Miss:
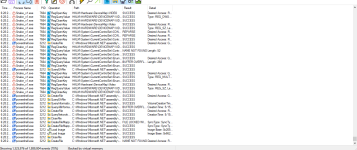
812c1bc73253ea51ba829be98d7c1af22c52fe8308014eca7d0dd6940dd3608c | Triage
Check this report malware sample 812c1bc73253ea51ba829be98d7c1af22c52fe8308014eca7d0dd6940dd3608c, with a score of 7 out of 10.
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
Quasar, caught by Avast(powershell):
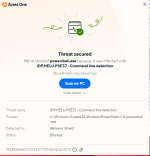
quasar | 99198643f2b0564539abec2e6e7ca8c7c455e203077b8751a9a8400807ad1ddc | Triage
Check this quasar report malware sample 99198643f2b0564539abec2e6e7ca8c7c455e203077b8751a9a8400807ad1ddc, with a score of 10 out of 10.
@SeriousHoax @silversurfer
Last edited:
Medieval Cracked.exe was detected by ESET and Bitdefender TS.Kaspersky is too good. Another fake game stealer using the same method(app.asar). Downloaded from itch.io, it's actually on the "New & Popular" page. On VT, Kaspersky caught it again
epsilon | 962c6df0b8ca065bd5df52e06c744c7795867aaacf856798e78cf27fecf3ea9d | Triage
Check this epsilon report malware sample 962c6df0b8ca065bd5df52e06c744c7795867aaacf856798e78cf27fecf3ea9d, with a score of 10 out of 10.tria.ge
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
Another one, Avast Miss:
View attachment 277174View attachment 277175
812c1bc73253ea51ba829be98d7c1af22c52fe8308014eca7d0dd6940dd3608c | Triage
Check this report malware sample 812c1bc73253ea51ba829be98d7c1af22c52fe8308014eca7d0dd6940dd3608c, with a score of 7 out of 10.tria.ge
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
Quasar, caught by Avast(powershell):
View attachment 277176
quasar | 99198643f2b0564539abec2e6e7ca8c7c455e203077b8751a9a8400807ad1ddc | Triage
Check this quasar report malware sample 99198643f2b0564539abec2e6e7ca8c7c455e203077b8751a9a8400807ad1ddc, with a score of 10 out of 10.tria.ge
@SeriousHoax @silversurfer
ESET had two detection via Command Line Scanner, one via AMSI.
Bitdefender Total Security blocked via its Command Line Scanner. FYI, BD Free doesn't have Command Line Scanner. So I can't tell if BD Free can detected it.
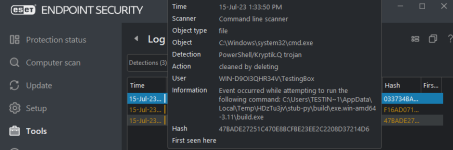
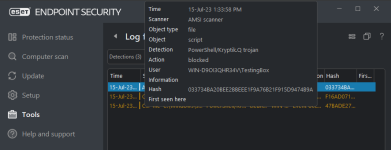
I hid the malicious code in the screenshots on purpose.
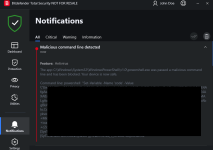
ESET missed, Snake_v1.exe.
Snake_v1.exe was caught by Bitdefender's Behavior Blocker and a malicious C2 was also blocked prior to that.

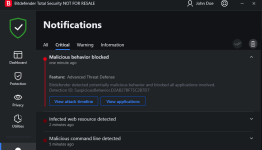
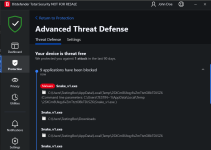
Microsoft Defender missed both Medieval Cracked.exe & Snake_v1.exe. Medieval Cracked.exe turned off MD's Cloud Protection, Auto sample submission and also added several file formats to its exclusions. So the malware could do anything it wanted.
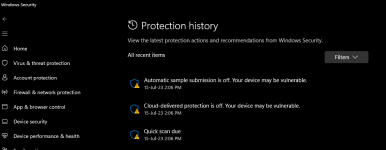
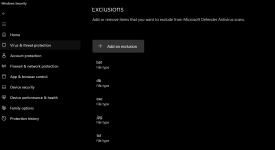
Later, I manually turned all protection on and removed the exclusions. Then when I clicked on a malicious file running on memory, MD woke up and detected a Backdoor and removed files related to it like scheduled tasks. But this detection doesn't matter. So failure for MD.
TBMSetup (1).exe was missed by all of MD, ESET and BD. I can't tell if it was able to steal data.
- Aug 17, 2014
- 12,726
- 123,827
- 8,399
My test with Bitdefender Free is still in progress... I will add details step by step 
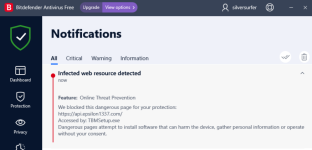
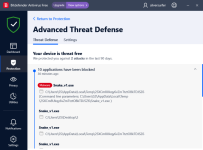
TBMSetup (1).exe => BD "Online Threat Prevention" blocked this URL:
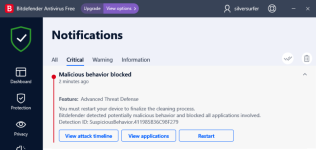
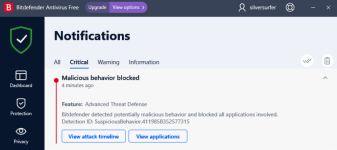
Medieval Cracked.exe => BD "Advanced Threat Defense" blocked/detected malicious behavior:
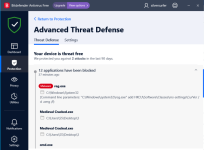
Snake_v1.exe => BD "Advanced Threat Defense" blocked/detected malicious behavior:
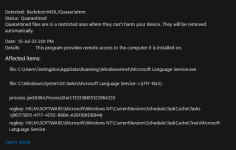
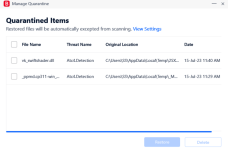
Bitdefender Quarantine: two files spawned/dropped by Medieval...exe & Snake...exe
TBMSetup (1).exe => BD "Online Threat Prevention" blocked this URL:

Medieval Cracked.exe => BD "Advanced Threat Defense" blocked/detected malicious behavior:


Snake_v1.exe => BD "Advanced Threat Defense" blocked/detected malicious behavior:


Bitdefender Quarantine: two files spawned/dropped by Medieval...exe & Snake...exe

Last edited:
Great insight, thanks!Medieval Cracked.exe was detected by ESET and Bitdefender TS.
ESET had two detection via Command Line Scanner, one via AMSI.
Bitdefender Total Security blocked via its Command Line Scanner. FYI, BD Free doesn't have Command Line Scanner. So I can't tell if BD Free can detected it.
View attachment 277183View attachment 277184View attachment 277185
View attachment 277179
I hid the malicious code in the screenshots on purpose.
ESET missed, Snake_v1.exe.
Snake_v1.exe was caught by Bitdefender's Behavior Blocker and a malicious C2 was also blocked prior to that.
View attachment 277180View attachment 277181View attachment 277182
Microsoft Defender missed both Medieval Cracked.exe & Snake_v1.exe. Medieval Cracked.exe turned off MD's Cloud Protection, Auto sample submission and also added several file formats to its exclusions. So the malware could do anything it wanted.
View attachment 277186View attachment 277187
Later, I manually turned all protection on and removed the exclusions. Then when I clicked on a malicious file running on memory, MD woke up and detected a Backdoor and removed files related to it like scheduled tasks. But this detection doesn't matter. So failure for MD.
View attachment 277188
TBMSetup (1).exe was missed by all of MD, ESET and BD. I can't tell if it was able to steal data.
- Status
- Not open for further replies.
You may also like...
-
Malware Analysis Another Evasive Discord Token Stealer Disguised as PC game 🎮☠️
- Started by Kongo
- Replies: 32
-
Hot Take Missed script malware by signature analysis
- Started by Parkinsond
- Replies: 100
-
