I noticed most won't delete because there are many programs that behave in a similar way to ransomware. File syncing programs do mass encrypt and delete files. Maintenence programs, Uninstallers, File encryption software, even web browsers frequently write, encrypt and delete files so unless there are additional signs of nefarious behavior, AVs will wait until there is an established behavioral pattern in the malware.
Hot Take Kaspersky and various other AVs can't detect simple ransomware script
- Thread starter Ahmed Uchiha
- Start date
- Featured
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
But, are .bat files can be trusted most of them used for bad purposes they look suspicious most of the time.I noticed most won't delete because there are many programs that behave in a similar way to ransomware. File syncing programs do mass encrypt and delete files. Maintenence programs, Uninstallers, File encryption software, even web browsers frequently write, encrypt and delete files so unless there are additional signs of nefarious behavior, AVs will wait until there is an established behavioral pattern in the malware.
- Apr 28, 2015
- 9,282
- 1
- 84,079
- 8,389
Acting as if SRP.But, are .bat files can be trusted most of them used for bad purposes they look suspicious most of the time.
Thank you so much for taking the time and effort to clarify I am sorry I am not tech savvy to analyze or fully understand what this code can do.
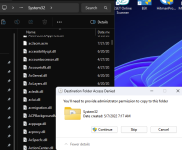
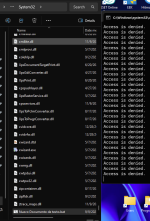
The posted BAT isn’t encrypting anything—it only renames files—so by Kaspersky’s classification it’s a benign/PUA-style script, not true ransomware; they reserve “malware” flags for code that actually encrypts, persists, or destroys. Bitdefender’s block reflects stricter heuristics on mass file ops, but that cuts both ways: BD has also missed live ransomware waves like Magniber variants before generic detection caught up. This is why single-sample anecdotes don’t prove superior protection—focus on layered behavior defenses and tested responses to real crypto‑ransomwareI found someone online create simple ransomware basic sample it encrypts local folder files into .txt extension but, Kaspersky couldn't protect the system against it but, Bitdefender detected the script and blocked it I didn't try ESET or Macafee but, it's disappointing that Kaspersky didn't pick it up and after reporting the code to Kaspersky they said it's safe.
this is the source code saved as .bat file if someone want to test
@echo off
setlocal enabledelayedexpansion
for %%f in (*.*) do (
ren "%%f" "%%~nxf.txt"
)
and this is the decryption key source code for this sample it should be saved as .bat and the password is: 123
@echo off
setlocal enabledelayedexpansion
set /p "input=enter password to unlock :"
if "%input%"=="123" (
echo password correct ....
for %%f in (*.txt) do (
set "name=%%~nf"
set "ext=%%~xf"
ren "%%f" "!name!"
)
echo done
)else (
echo wrong password ....
)
pause
I want to know why Kaspersky virus lab flagged the sample as safe although it can encrypt files in the same folder which can cause data loss and Bitdefender detects it as malware.
Also, here’s a YT link showing BD failing against Magniber in 2022 :
There are documented user reports that Bitdefender struggled with Magniber waves until generic behavior detections were improved; detection lag without signatures was noted in mid‑2022 discussions.
Magniber campaigns abused SmartScreen and MSI/JS delivery chains; even strong products had blind spots until Microsoft and vendors pushed fixes and updated behavior signatures.
In hands-on stress tests, outcomes can swing: some videos show Bitdefender failing against ransomware in certain scenarios, while others show strong stops; likewise Kaspersky sometimes blocks late in execution but prevents data loss. The key is layered behavior blocking, not one-off anecdotes.
This script was probably developed for a genuine reason.
I don’t wanna say how many times I’ve needed to rename files or modify extensions.
For example I developed a platform that used xml files. Later on I decided I wanna give them a custom *hadb extension. I am not gonna go and rename one be one, it is easier with a script.
Not every change in files can be classified malicious and not everything on these repositories is necessarily malicious. The context is very important.
I don’t wanna say how many times I’ve needed to rename files or modify extensions.
For example I developed a platform that used xml files. Later on I decided I wanna give them a custom *hadb extension. I am not gonna go and rename one be one, it is easier with a script.
Not every change in files can be classified malicious and not everything on these repositories is necessarily malicious. The context is very important.
I agree... it probably was developed for a genuine reason, but this file is not safe to let lay around just anywhere, or released into the wild. I have tons of files that I use for development that are perfectly safe in the right hands, but outside of that, they are anything but safe.This script was probably developed for a genuine reason.
I don’t wanna say how many times I’ve needed to rename files or modify extensions.
For example I developed a platform that used xml files. Later on I decided I wanna give them a custom *hadb extension. I am not gonna go and rename one be one, it is easier with a script.
Not every change in files can be classified malicious and not everything on these repositories is necessarily malicious. The context is very important.
This is why it is better to use Safe vs Not Safe for the final verdict, instead of Malicious vs Benign.
This file is not malicious, but it is also Not Safe.
Anyone that calls this file Safe needs to do the honorable thing and run it on their favorite folder of their computer
Well, the renaming can be reversed with another script.I agree... it probably was developed for a genuine reason, but this file is not safe to let lay around just anywhere, or released into the wild. I have tons of files that I use for development that are perfectly safe in the right hands, but outside of that, they are anything but safe.
This is why it is better to use Safe vs Not Safe for the final verdict, instead of Malicious vs Benign.
This file is not malicious, but it is also Not Safe.
Anyone that calls this file Safe needs to do the honorable thing and run it on their favorite folder of their computer.
I also don't see any reason why a user would go around, download scripts and run them.
The file was not released in the wild, it was uploaded on malware repository. There is no social engineering or attempts to trick the users into downloading or executing this script in the wild.
Totally agree.Well, the renaming can be reversed with another script.
I also don't see any reason why a user would go around, download scripts and run them.
The file was not released in the wild, it was uploaded on malware repository. There is no social engineering or attempts to trick the users into downloading or executing this script in the wild.
We also need to keep in mind that this script does not do anything useful. It would be one thing if it renamed the extension of all of the files in the directory, we all need to do that from time to time. But that is not what it does... it adds a .txt extension to the file name, which serves absolutely no legitimate purpose. Here is Sirius's take... keep in mind that we do not use the term "Not Safe" within the instructions, we use "Malicious" to avoid confusion within the model, then convert it to "Not Safe" later.
Analysis Summary
The script disables echo, enables delayed variable expansion (unnecessary here but common in batch malware to support string manipulation), then iterates over every file in the current directory and renames it by appending “.txt” to its existing name. This has the net effect of hiding the original extension and making every file appear to be a text file. While the operation is reversible and does not destroy data, it is a textbook evasion trick: it breaks file-type associations, hinders forensic triage, and can trick users into double-clicking what they believe are harmless documents. The lack of any legitimate business purpose, the absence of path or extension filtering, and the intentional obfuscation of every file’s true nature all point to malicious intent. No signed payload is present, but the script itself is the payload—its only function is to mask files for subsequent stages or user deception.
Malware type: PUP
Malware name: ExtensionMasquerader.Batch
Final verdict: Malicious with 92% confidence.
It's about weaponise the script it's like using legitimate app to do unsafe things (using bitlocker or legitimate process to encrypt files) like filess malware I guess and process hijack etc.Well, the renaming can be reversed with another script.
I also don't see any reason why a user would go around, download scripts and run them.
The file was not released in the wild, it was uploaded on malware repository. There is no social engineering or attempts to trick the users into downloading or executing this script in the wild.
But, of course malware analyst do know more than me I am just saying thoughts but, reality is another thing

What Are LOLBins and How Do Attackers Use Them in Fileless Attacks?
Living off the land (LOL) describes using trusted, pre-installed system tools for malware propagation
My curiosity got the best of me and I wanted to see what would happen if the file extensions were renamed to .txt instead of adding the .txt extension to the end. So I would agree with this verdict, but there are very strong points for both sides, and there is probably not one clear answer either way.
I changed the script to...
@echo off
setlocal enabledelayedexpansion
for %%f in (*.*) do (
ren "%%f" "%%~nf.txt"
)
Analysis Summary
The script is a short batch file that iterates over every file in its working directory and renames each one by stripping its original extension and appending “.txt”. It does not inspect file content, does not download or execute anything, and does not attempt to hide its actions. The only functional consequence is that every file becomes a “.txt” file, which could break file-type associations or obscure the original nature of executables, but this is a simple, reversible rename operation rather than destructive payload delivery or system compromise. There is no obfuscation, no living-off-the-land abuse beyond standard “for” iteration, and no evidence of malicious intent such as data exfiltration, persistence, or code injection.
Final verdict: Safe with 90% confidence.
I changed the script to...
@echo off
setlocal enabledelayedexpansion
for %%f in (*.*) do (
ren "%%f" "%%~nf.txt"
)
Analysis Summary
The script is a short batch file that iterates over every file in its working directory and renames each one by stripping its original extension and appending “.txt”. It does not inspect file content, does not download or execute anything, and does not attempt to hide its actions. The only functional consequence is that every file becomes a “.txt” file, which could break file-type associations or obscure the original nature of executables, but this is a simple, reversible rename operation rather than destructive payload delivery or system compromise. There is no obfuscation, no living-off-the-land abuse beyond standard “for” iteration, and no evidence of malicious intent such as data exfiltration, persistence, or code injection.
Final verdict: Safe with 90% confidence.
For me if this happened to my files I would panic thinking my files encrypted and wouldn't figure it out that's just renaming or changing extension and of course would ask someone to helpWell, the renaming can be reversed with another script.
I also don't see any reason why a user would go around, download scripts and run them.
The file was not released in the wild, it was uploaded on malware repository. There is no social engineering or attempts to trick the users into downloading or executing this script in the wild.
But that’s why you are not supposed to go around and download/execute scripts. As part of a real attack, there will be other indicators like persistence, malicious website for distribution, code injection, downloading and dropping of content and so on. In this case, it will become suspicious/malicious. Right now, it’s harmless script.For me if this happened to my files I would panic thinking my files encrypted and wouldn't figure it out that's just renaming or changing extension and of course would ask someone to help
Most likely someone wanted to test/debug the sandboxes, or some type of behavioural rules they’ve got and uploaded this simple file. Though this intelligence is used in many third-party open and closed source projects and the upload of benign files is strictly prohibited. The account needs to be reported for abusing the abuse.ch rules, assuming that the file was taken from there.My curiosity got the best of me and I wanted to see what would happen if the file extensions were renamed to .txt instead of adding the .txt extension to the end. So I would agree with this verdict, but there are very strong points for both sides, and there is probably not one clear answer either way.
I changed the script to...
@echo off
setlocal enabledelayedexpansion
for %%f in (*.*) do (
ren "%%f" "%%~nf.txt"
)
Analysis Summary
The script is a short batch file that iterates over every file in its working directory and renames each one by stripping its original extension and appending “.txt”. It does not inspect file content, does not download or execute anything, and does not attempt to hide its actions. The only functional consequence is that every file becomes a “.txt” file, which could break file-type associations or obscure the original nature of executables, but this is a simple, reversible rename operation rather than destructive payload delivery or system compromise. There is no obfuscation, no living-off-the-land abuse beyond standard “for” iteration, and no evidence of malicious intent such as data exfiltration, persistence, or code injection.
Final verdict: Safe with 90% confidence.
Yes, there are not a lot of benign files on malware repositories, but there are certainly some.Most likely someone wanted to test/debug the sandboxes, or some type of behavioural rules they’ve got and uploaded this simple file. Though this intelligence is used in many third-party open and closed source projects and the upload of benign files is strictly prohibited. The account needs to be reported for abusing the abuse.ch rules, assuming that the file was taken from there.
Just curious, there is probably not a correct answer to this, but what happens when the website that hosts the dropped malicious payload is taken down, is the original dropper then considered benign? Or, if a certain malware is being analyzed in a sandbox, and it has dependencies that are not included in the sandbox analysis (so it cannot fully execute), is that sample benign?
So any time you see any kind of coding in any script ps1 or bat and so forth, you consider them malicious ? It may sound harsh, but you better learn to program, sit in a computer science 101 at a university. You don't need to pass the entrance test, just get the class schedule to find the classroom and go sit down. Most professors allow that. Malware detection Requires one to understand code a little bit.Thank you so much for taking the time and effort to clarify I am sorry I am not tech savvy to analyze or fully understand what this code can do.
Last edited:
That’s a very wide subject. Typically, malware aims to be a self contained project, relying on dependancies makes it fragile and adds more ifs and buts to an already huge list of them. Malware will either come in an archive with all dependancies, or it will rely on tools and utilities already provided by the OS. Sandboxes typically provide the dependancies.Yes, there are not a lot of benign files on malware repositories, but there are certainly some.
Just curious, there is probably not a correct answer to this, but what happens when the website that hosts the dropped malicious payload is taken down, is the original dropper then considered benign? Or, if a certain malware is being analyzed in a sandbox, and it has dependencies that are not included in the sandbox analysis (so it cannot fully execute), is that sample benign?
When the website hosting a payload is down, the payload is still malicious. But this script is not a payload, if you define every 3 lines of code that cause mere inconvenience as malware, then you may as well stop paying for your broadband and disconnect.
It is not even a malware artefact, it’s something someone designed for a purpose.
There are many files like this.
McAfee and ZoneAlarm Threat Emulation conclude the script is clean. So does my upcoming Orion engine.
You may also like...
-
Serious Discussion Data Collection Core Principles (Security Software)
- Started by Trident
- Replies: 7
-
Serious Discussion Deep Research: Bitdefender Protection Technologies
- Started by Trident
- Replies: 6
-
Serious Discussion Deep Research: Trend Micro VSAPI and ATSE Release History and Modus Operandi
- Started by Trident
- Replies: 7
-
-
AV-TEST 26 Security Solutions Undergo an Advanced Threat Protection Test Against Ransomware
- Started by Gandalf_The_Grey
- Replies: 5